Goal
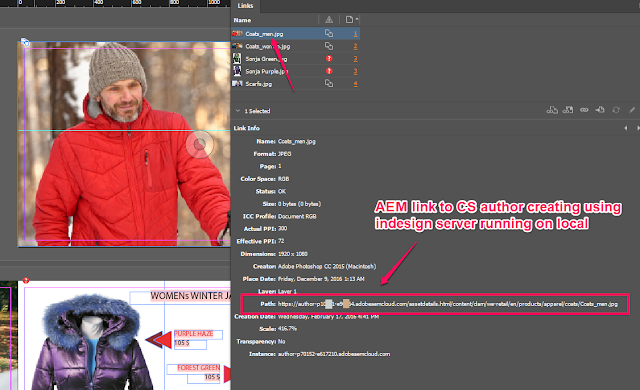
Asset Link in InDesign supports creating AEM Links (Link is an AEM path, not local file path). Documents created with AEM Links can be opened on other designers desktops with No Missing Links Warning in Links Panel
The following solution could be useful when legacy documents with local fs links (or documents created by design agencies with no access to AEM) are uploaded to AEM and a user expects AEM to automatically convert the local links to AEM links
1) Design agency creates documents with local links (placing images from file system, not AEM)
2) Documents are uploaded to local AEM SDK or any AEM with access to InDesign Server
3) Media Extraction Step of DAM Update Asset Workflow is updated with Relink Script /apps/settings/dam/indesign/scripts/local-to-aem-relink.jsx
4) getAEMPaths() of local-to-aem-relink.jsx, executing in InDesign Server makes a Query Builder call to AEM, fetch the respective paths for local links...
5) If AEM host/domain is provided in script local-to-aem-relink.jsx (RELINK_HOST_PREFIX), links are rewritten using the specified AEM host, else the AEM host initiating InDesign server request is used in link path...
6) Relinked document is uploaded to AEM as a rendition with suffix -with-aem-links.indd
7) A Post processing workflow step can create new indesign document by moving/copying the rendition and delete the document with local links or keep them both, based on the necessity....
Demo | Package Install | Github
Solution
1) Add the Relink Script in CRXDe /apps/settings/dam/indesign/scripts/local-to-aem-relink.jsx
(function () {
var RELINK_HOST_PREFIX = "",
QUERY_BUILDER_PATH = "/bin/querybuilder.json?path=/content/dam&type=dam:Asset",
AEM_RELINKED_DOC_SUFFIX = "-with-aem-links.indd",
AEMS_PROTOCOL = "aems://";
try{
app.consoleout('Checking if relinking to AEM links is required for : ' + resourcePath);
var links = document.links,
hostPrefix = RELINK_HOST_PREFIX;
if(!hostPrefix){
hostPrefix = AEMS_PROTOCOL + host;
}
if(!hasAEMLinks(links)){
app.consoleout('Document contains local links, AEM relinking required : ' + resourcePath);
var aemPaths = getAEMPaths(links);
relinkLocalToAEM(links, aemPaths, hostPrefix);
var fileName = resourcePath.substring(resourcePath.lastIndexOf ('/') + 1, resourcePath.lastIndexOf ('.') ),
relinkedFileName = fileName + AEM_RELINKED_DOC_SUFFIX,
relinkedFile = new File( sourceFolder.fullName + "/" + relinkedFileName);
document.save(relinkedFile);
app.consoleout('Uploading relinked doc to : ' + target + '/jcr:content/renditions' + ", as : " + relinkedFileName);
putResource(host, credentials, relinkedFile, relinkedFileName, "application/x-indesign", target);
}else{
app.consoleout('Document contains AEM links, relinking to AEM NOT required : ' + resourcePath);
}
}catch(err){
app.consoleout("Error relinking document : " + resourcePath + ", error : " + err);
}
function hasAEMLinks(links){
var containsAEMLinks = false;
for(var i = 0; i < links.length; i++ ){
if(links[i].linkResourceURI.indexOf(AEMS_PROTOCOL) == 0){
containsAEMLinks = true;
break;
}
}
return containsAEMLinks;
}
function relinkLocalToAEM(links, aemPaths, hostPrefix){
for(var i = 0; i < links.length; i++ ){
var link = links[i],
aemPath = aemPaths[link.name];
if(!aemPath){
app.consoleout("Could not find aem path for file : " + link.name);
continue;
}
var aemLink = hostPrefix + aemPath;
try{
app.consoleout("Relinking to aem with uri : " + aemLink);
link.reinitLink(aemLink );
}catch(err){
app.consoleout("error relinking : " + err);
return;
}
}
}
function getInDesignDocRealAEMPath(){
var fileName = resourcePath.substring(resourcePath.lastIndexOf ('/') + 1 ),
query = QUERY_BUILDER_PATH + "&nodename=" + fileName;
var hitMap = fetchJSONObjectByGET(host, credentials, query);
if(!hitMap || (hitMap.hits.length == 0)){
return;
}
var aemPath;
for(var i = 0; i < hitMap.hits.length; i++ ){
aemPath = hitMap.hits[i]["path"];
}
return aemPath;
}
function getAEMPaths(links){
var query = QUERY_BUILDER_PATH + "&group.p.or=true",
aemPaths = {};
for(var i = 0; i < links.length; i++ ){
query = query + "&group." + (i + 1) + "_nodename=" + links[i].name;
}
var hitMap = fetchJSONObjectByGET(host, credentials, query);
if(!hitMap || (hitMap.hits.length == 0)){
app.consoleout('No Query results....');
return;
}
for(var i = 0; i < hitMap.hits.length; i++ ){
aemPaths[hitMap.hits[i]["name"]] = hitMap.hits[i]["path"];
}
return aemPaths;
}
}());
2) Add the relink script path in the Media Extraction Step of DAM Update Asset workflow http://localhost:4502/editor.html/conf/global/settings/workflow/models/dam/update_asset.html
3) Sample InDesign document with local links....
4) On upload, processed by InDesign Server, document with AEM links gets created as rendition of original document....