For authenticating end users AEM Publish can be configured with SAML2.0 connecting to an IDP to authenticate users and create authenticated session in AEM, for more info check documentation. This post is on investigating SAML connection/assertions issues by redirecting responses from customer's IDP to local publish AEM sdk (instead of cloud services publish instance). Investigating assertions on a local instance by attaching debugger can be much faster compared to downloading logs from cloud manager where the issue exists...
1) As all AEM cloud services instances are on https, enable the local dispatcher sdk to run on https. For more details check https://experience-aem.blogspot.com/2022/10/aem-cloud-service-setup-local-sdk-docker-https-ssl.html
2) Get the SAML specific values from Environment Configuration of customer's publish instance...
3) Add the environment variables in publish start script. Attach a debugger to local AEM SDK Publisher...
REM DEV
set SAML_AEM_ID=https://publish-pxxxxx-exxxxx.adobeaemcloud.com/
set SAML_IDP_CERT_ALIAS=certalias___999999999999999
set SAML_IDP_URL=https://login.microsoftonline.com/xxxx-xxxx-xxx-xxx-xxxxxxxx/saml2
set SAML_IDP_REFERRER=login.microsoftonline.comC:/Progra~1/Java/jdk-11.0.6/bin/java -Xdebug -Xrunjdwp:transport=dt_socket,address=6006,suspend=n,
server=y -XX:MaxPermSize=512m -Xmx1024M -Doak.queryLimitInMemory=500000 -Doak.queryLimitReads=500000
-Dsling.run.modes=publish -jar aem-sdk-quickstart-2022.9.8630.20220905T184657Z-220800-p4503.jar -nofork
4) In Local Publish AEM SAML Authentication handler configuration (com.adobe.granite.auth.saml.SamlAuthenticationHandler~eaem.cfg.json) set useEncryption to false (so we only need the truststore configuration and not private key configuration of authentication-service user making it a simpler setup...)
........
........
"idpUrl": "$[env:SAML_IDP_URL;default=https://myapps.microsoft.com/signin/xxx-xxx-xxx-xxx-xxxxxxxx?tenantId=xxxx-xxx-xxx-xxx-xxxxxxx]",
"serviceProviderEntityId": "$[env:SAML_AEM_ID;default=https://publish-pxxxxx-exxxxx.adobeaemcloud.com]",
"useEncryption": false,
"createUser": true,
........
........
5) Get the trust store from customer's author instance crxde (generally the same certificate is activated to publish). Package it up on customer's author with filter /etc/truststore and install the package on local AEM publish...
6) The encrypted keystorePassword is unique to each AEM instance (encrypted/decrypted using the hmac and master keys available on file system of bundle Adobe Granite Crypto Bundle Key Provider), so the keystorePassword exported from customer's AEM instance cannot be decrypted using the crypto keys of local AEM so we need to encrypt the keystorePassword using local AEM keys and add it in /etc/truststore
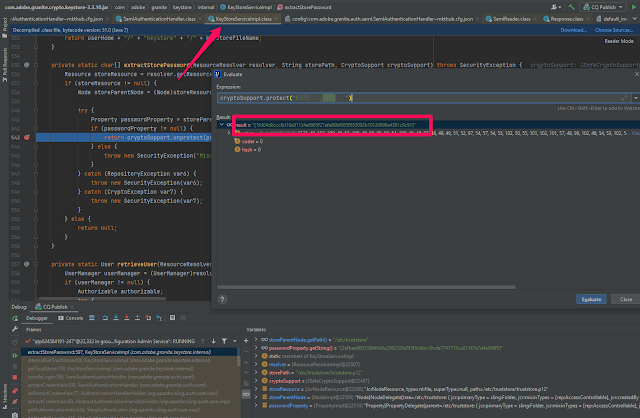
7) Connect the IDE debugger to local publish instance, execute a simple POST call to http://localhost:4503/content/marketing-hub/saml_login and debug method extractStorePassword() of class com.adobe.granite.keystore.internal.KeyStoreServiceImpl; use cryptoSupport.protect("plainPasswordOfTrustStore") code statement to generate the local AEM specific encrypted keystorePassword
8) Once you have the keystorePassword of trust store encrypted using local AEM keys, open crxde and add it in /etc/truststore@keystorePassword, save..
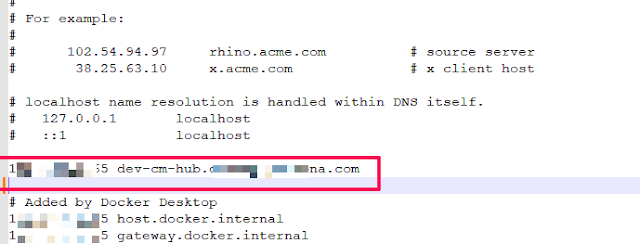
9) Next step is to spoof the requests that are originally for customer's AEM env. If you are on windows open the hosts file c:\Windows\System32\Drivers\etc\hosts and add the customer's AEM domain entry with your local machine's IP, save and flush the DNS cache using command prompt ipconfig /flushdns
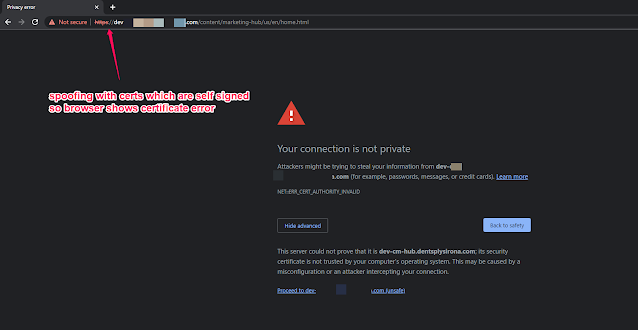
10) Configuration is now complete and you can try the local AEM publish to customer's IDP authentication flow, accessing local AEM on https using customer's AEM domain name...
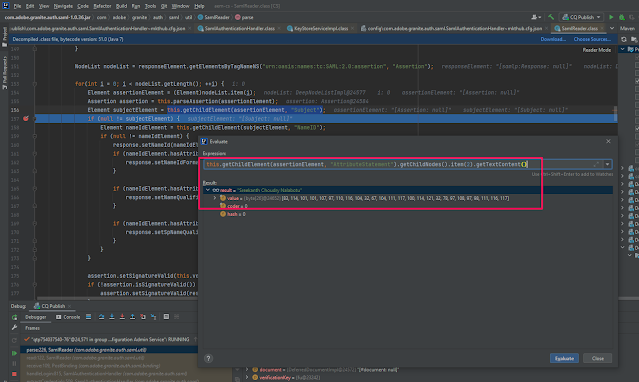
11) To read the SAML Assertions put a debug point in parse() method of com.adobe.granite.auth.saml.util.SamlReader
12) With successful IDP authentication you should see the SAML protected page on local AEM publish...





No comments:
Post a Comment